Copy pasted from:
http://citrixsolutions.blogspot.com/2012/04/receiver-storefront-10-step-by-step.html
Refer to original link for more solutions.
This article will show how to quickly create a StoreFront 1.0 Proof Of Concept.
As per Citrix eDocs:
“Receiver Storefront provides authentication and resource delivery infrastructure for Citrix Receiver, enabling you to create centralized enterprise stores to deliver desktops, applications, and other services to users on any device, anywhere.”
Source: Citrix eDocs
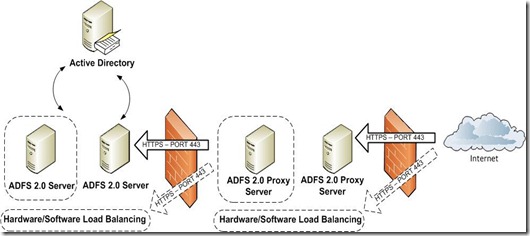
The StoreFront is a component of the new Citrix CloudGateway Express and Enterprise infrastructures; it provides authentication and content delivery (XenApp apps, XenDesktop desktops, SaaS…) to Citrix Receivers for any device and platform.
StoreFront will be the replacement of what we now call the Web Interface; indeed, the WI should be replaced by all customers by 2015. StoreFront gives users the opportunity to choose which applications to have in their ‘home page’. Such information are stored in the StoreFront DB and roams along with users between different devices and OSs. In this way, users will have their settings following them on every device, everywhere.
This article is intended to show how to quickly create a POC and not how to install it in a production environment.
This Guide is divided into three parts:
- 1 – StoreFront Installation;
- 2 – StoreFront Configuration – HTTP;
- 3 – StoreFront Configuration – HTTPS.
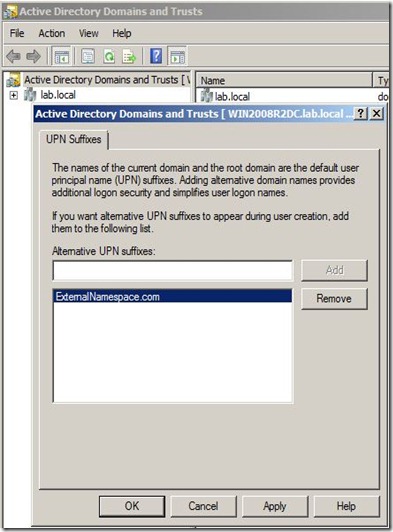
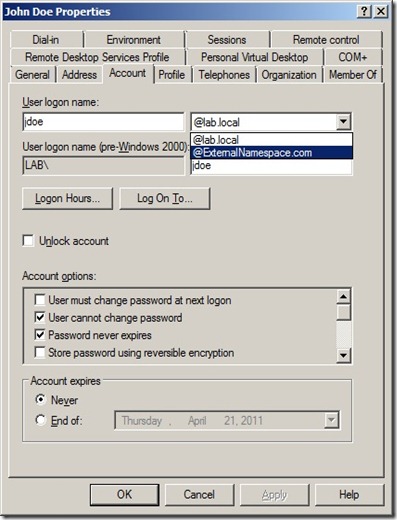
As you might know, by default the latest Citrix Receiver will not connect to a non-secure service site, that’s why I included the HTTPS configuration part. Anyway, if you are interested in allowing http access instead of https, you can give a look at this article:geekshangout.com.
1 – StoreFront Installation
Prerequisites: the most important prerequisite is SQL Express, for the others take a look at Citrix eDocs!
1) First of all download the software installer from Citrix.com and save it on your server;
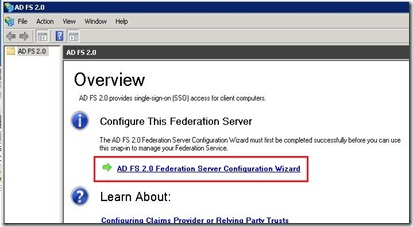
2) Double click on the icon, accept the license agreement and click Next:
3) The IIS role will be installed automatically, click Next and then Install:
4) Click on Finish when the installation completes, you will be redirected to the Citrix Receiver StoreFront Console.
2 – StoreFront Configuration – HTTP
We will now go through the configuration of StoreFront as an HTTP site;
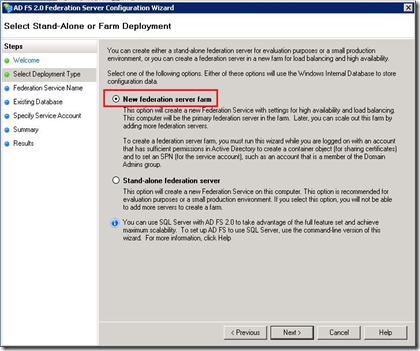
1) In the console select ‘Deploy a single server’:
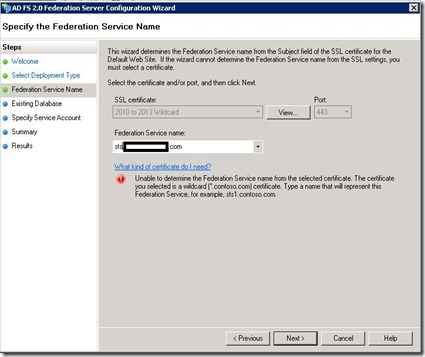
2) Type in the server URL you want to use and click Create:
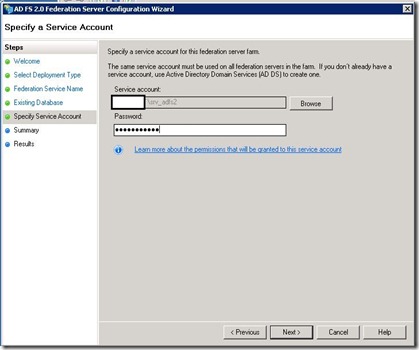
3) Now we have to create an authentication service for the site, to do that click Create Service in the Authentication box:
4) Select the authentication method you want to use and click Create:
5) Now we have to create a store for the site, which is a container of applications and desktops; click on Create Store and enter the name you wish to use:
6) Now enter the information of the XenApp or XenDesktop farms you want to configure and click on Create; if you need to, you can add more farms later:
7) Now click on Create Site in the ‘Receiver for Web’ box in order to create a ‘Web Site’ which will provide the ‘Web Receiver’ feature to users:
9) Insert your User name and Password and Log On:
10) Click on Add Apps and chose the applications/desktops you want to have on your personal page:
11) On your home page you will see the apps you chose, just click on one of them to launch it!
12) From this page you can automatically activate (that is, configure) the receiver installed on your device; to do that click on the ‘Activate Citrix Receiver for your Desktop’ and select Activate:
13) Click open on the IE alert:
This is the content of the file:
It’s actually an XML file which instructs the Citrix Receiver on how to connect to the store.
3 – StoreFront Configuration – HTTPS
We will now go through the configuration of StoreFront as an HTTPS site. In order to do that, you have to bind the HTTPS protocol (along with a valid server certificate) to your Default Web Site in the IIS management console. Once that is done, you can proceed with the following tasks (which are exactly the same as for the HTTP configuration):
1) Start the deployment process and choose ‘Deploy a single server’:
2) Then create the authentication service:
3) Then create the store:
4) And then the HTTPS web site:
Your site is now configured to be accessed through HTTPS!!!