Copy-pasted from blog - http://howdouc.blogspot.com/2011/04/active-directory-federation-services_11.html
Active Directory Federation Services (ADFS) 2.0 with Office 365: Part 2 – Configuring
Assumptions:
- Domain has been added and verified in the Office 365 Admin portal
- Directory Sync Tool is installed and configured
- 2 Windows 2008 R2 servers are built and prepared to install ADFS 2.0
- Internal ADFS server is joined to the domain
- Proxy ADFS server is not joined to domain and located in perimeter network
- Necessary firewall ports are open from the Internet to ADFS Proxy server (port 443)
- Necessary firewall ports are open from ADFS Proxy server to internal ADFS server (port 443)
- External DNS record has been implemented for ADFS (our example will use sts.UPNdomain.com)
- Add
UPN Suffix to AD and configure for each user (this is required if your
AD is using a non-routable domain internally like .local or .priv)
- UPNs used for identity federation can only contain letters, numbers, periods, dashes and underscores.
- Open AD Domains and Trusts tool
- Right-click AD Domains and Trusts and click Properties
- On the UPN suffixes tab, type the alternative UPN suffix for the forest and then click Add
- Repeat to add additional UPN suffixes
- Open user properties, navigate to Account Tab.
- Select the external namespace UPN for the “User logon name”
- Create service account for ADFS – this can be a regular Domain User, no special permissions needed.
- Add internal ADFS server(s) to AD forest
- Download ADFS 2.0 RTW (HERE). During the install process, the following Windows components will be automatically installed:
- Windows PowerShell
- .NET Framework 3.5 SP1
- Internet Information Services (IIS)
- Windows Identity Foundation
- Download Microsoft Online Services Identity Federation Management Tool (32-bit or 64-bit)
- (Optional) Install and configure SQL Server 2005 or 2008 if your organization has more than 30,000 users who will use Office 365
- Configure external DNS A record for ADFS Proxy (ex. Sts.domain.com)
- Double-click AdfsSetup.exe (this is the ADFS 2.0 RTW download)
- Click Next on the Welcome Screen and Accept the License Agreement
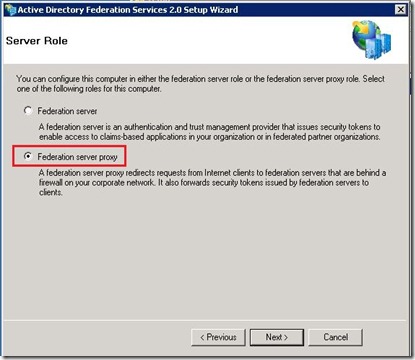
- On the Server Role Option screen, select Federation Server
- Finish the rest of the wizard, this will install any necessary prerequisites
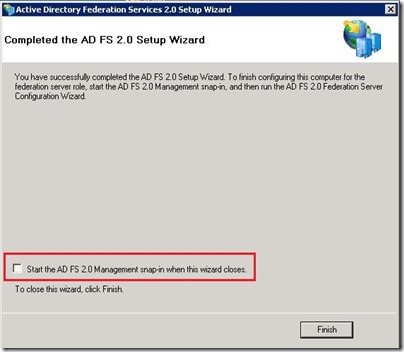
- At the end of the wizard, uncheck box to Start the ADFS 2.0 Management Snap-in
- Request and provision public certificate through IIS
- Bind certificate to IIS on port 443
- Configure ADFS utilizing ADFS 2.0 Management
- Select ADFS 2.0 Federation Server Configuration Wizard
- Select Create a new Federation Service
- Select New Federation server farm (this is recommended even if you plan on installing only one server in case in the future you want to add another server)
- Select the public certificate and validate the Federation Service name. This will automatically fill in the name on the certificate Subject Name. If a wildcard certificate is used, you must enter the name for the Federation Service.
- Enter in the service account credentials that were created earlier
- Finish Wizard
- Run Office 365 Desktop Setup from portal
- Install Identity Federation Management Tool (FederationConfig.msi, use default install parameters)
- Enable Identity Federation within Office 365 portal for your domain
- Launch the Identity Federation Management Tool
- Type $cred=Get-Credential and press Enter
- Enter you Microsoft Online Services administrator logon and password and click ok
- Type Set-MSOLContextcredential –msolAdminCredentials $cred –LogFile c:\logfile.log and press enter
- Type Add-MSOLFederatedDomain –domainname UPNdomain.com
- If prompted that the domain already exists as a standard domain, type Convert-MSOLDomainToFederated –domainname UPNdomain.com
- Type Update-MSOLFederatedDomain –domainname UPNdomain.com
- Verify Identity Federation Functionality
- Export public certificate from ADFS internal server and copy to proxy server
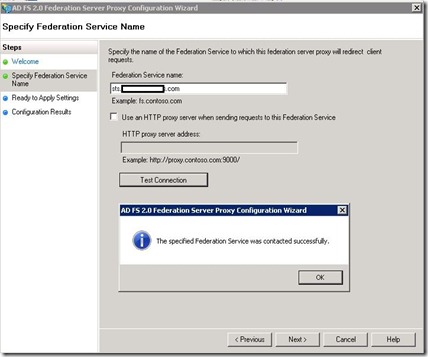
- Validate DNS resolution of sts.UPNdomain.com resolves to internal ADFS server from ADFS Proxy Server (a HOST file can be used for this if needed)
- Validate DNS resolution of sts.UPNdomain.com resolves to external A record from an internet PC
- Double-click AdfsSetup.exe (this is the ADFS 2.0 RTW download)
- Click Next on the Welcome Screen and Accept the License Agreement
- On the Server Role Option screen, select Federation Server Proxy
- Finish the rest of the wizard, this will install any necessary prerequisites
- At the end of the wizard, uncheck box to Start the ADFS 2.0 Management Snap-in
- Import certificate in IIS and bind certificate to Default Web Site
- Configure ADFS proxy by selecting ADFS 2.0 Federation Server Proxy Configuration Wizard
- Finish Wizard
- Log into portal with UPN credentials. Note that once the UPN login is entered, the password field is grayed out and a link activates to log into the ADFS server













You guys allow it to be quite simple for all your folks available.
ReplyDeleteCloud Migration
that was really nice one keep this work up we provide you all the services as we mentioned above.
ReplyDeleteLED LCD Repairing Institute
LED LCD Repairing Institute
LED LCD Repairing Institute
mobile repairing institute in nirman vihar
that looks like a great blog love this type of blogs.
ReplyDeletelaptop on rent in noida
projector on rent in noida
we are the best digital marketing institute in Delhi. by the way that is a nice post.
ReplyDeletedigital marketing course in ghaziabad
Thank you so much for sharing that amazing post with us. We will stay connected with your blogs for the future posts.Looking for the z hire zumiez com from Zumiez com? Try our products & automate all the IT account creation process for exchange mailbox, & active directory!
ReplyDeleteThanks for sharing active directory management tips. for more info i rfer cion systems active directiry mangement tools in USA.
ReplyDeleteWELCOME TO OUR INSTITUTE
ReplyDeleteAIDM is a premier institute in various digital marketing domains like SEO, SMO, PPC, ORM, Google Analytics, Email Marketing, Affiliate Marketing and Content Marketing.
AIDM ADDRESS :- A-13, Mohan Park, Laxmi Nagar Delhi - 110092
+91-9205903598
Mon to Sat 9am to 6 pm
info@aidm.org.in
Send us your query anytime!