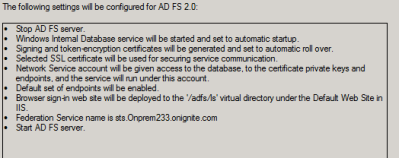
Copy-pasted from blog - http://blogs.southworks.net/mwoloski/2009/07/17/getting-a-token-from-adfs-ex-geneva-server-using-wcf/
I’ve been doing some tests to get a token from ADFS (Geneva Server) using Windows Identity Foundation WSTrustClient. In this case we are using the UserNameMixed endpoint that expects a WS-Security UsernameToken (notice the MessageCredentialType.UserName).
I’ve been doing some tests to get a token from ADFS (Geneva Server) using Windows Identity Foundation WSTrustClient. In this case we are using the UserNameMixed endpoint that expects a WS-Security UsernameToken (notice the MessageCredentialType.UserName).
internal static ClaimsIdentityCollection RequestTokenWithUsernameMixed()
{
var binding = new WS2007HttpBinding(SecurityMode.TransportWithMessageCredential, false);
binding.Security.Message.ClientCredentialType = MessageCredentialType.UserName;
binding.Security.Message.EstablishSecurityContext = false;
var credentials = new ClientCredentials();
credentials.UserName.UserName = "Mary";
credentials.UserName.Password = "Passw0rd!";
var endpoint = "https://mygenevaserver/Trust/13/UsernameMixed";
var client = new WSTrustClient(binding, new EndpointAddress(new Uri(endpoint)), TrustVersion.WSTrust13, credentials);
var request = new RequestSecurityToken();
request.RequestType = "http://schemas.microsoft.com/idfx/requesttype/issue";
request.AppliesTo = new EndpointAddress("http://localhost/activerp");
var token = client.Issue(request) as GenericXmlSecurityToken;
var claims = token.ToClaimsIdentityCollection(TrustVersion.WSTrust13, CertificateUtility.GetCertificate(StoreName.My, StoreLocation.LocalMachine, "CN=Geneva Signing Certificate - WIN-66EYOLL2BVY"), CertificateUtility.GetCertificate(StoreName.My, StoreLocation.LocalMachine, "CN=WMSvc-WIN-66EYOLL2BVY"));
return claims;
}
Here is another one using the WindowsMixed endpoint (notice the MessageCredentialType.Windows and no username and password set)internal static ClaimsIdentityCollection RequestTokenWithWindowsMixed()
{
var binding = new WS2007HttpBinding(SecurityMode.TransportWithMessageCredential, false);
binding.Security.Message.ClientCredentialType = MessageCredentialType.Windows;
binding.Security.Message.EstablishSecurityContext = false;
var credentials = new ClientCredentials();
var endpoint = "https://mygenevaser/Trust/13/WindowsMixed";
var client = new WSTrustClient(binding, new EndpointAddress(new Uri(endpoint)), TrustVersion.WSTrust13, credentials);
var request = new RequestSecurityToken();
request.RequestType = "http://schemas.microsoft.com/idfx/requesttype/issue";
request.AppliesTo = new EndpointAddress("http://localhost/activerp");
var token = client.Issue(request) as GenericXmlSecurityToken;
var claims = token.ToClaimsIdentityCollection(TrustVersion.WSTrust13, CertificateUtility.GetCertificate(StoreName.My, StoreLocation.LocalMachine, "CN=Geneva Signing Certificate - WIN-66EYOLL2BVY"), CertificateUtility.GetCertificate(StoreName.My, StoreLocation.LocalMachine, "CN=WMSvc-WIN-66EYOLL2BVY"));
return claims;
}
You can use this together with the CreateChannelWithIssuedToken extension method